Social media data analysis with Graph Neural Networks (GNN)-2
VASE: A Twitter-based Vulnerability Analysis and Score Engine
Citation: Haipeng Chen, Jing Liu, Rui Liu, Noseong Park, and V. S. Subrahmanian. “VEST: a system for vulnerability exploit scoring & timing.” In Proceedings of the 28th International Joint Conference on Artificial Intelligence, pp. 6503-6505. AAAI Press, 2019.
Highlights
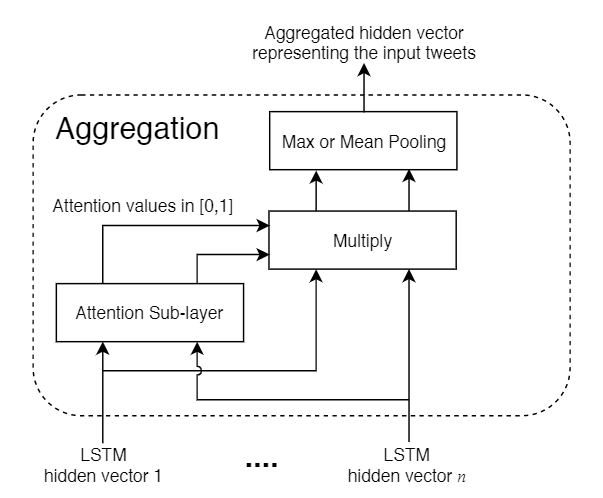
- Proposed a novel attention-based input embedding layer which includes a bi-directional long short term memory (LSTM) network and an attention network to extract vulnerability-related information from tweet texts
- Integrated the proposed input embedding layer with one state-of-the-art graph convolution neural network for predicting the severity of vulnerabilities
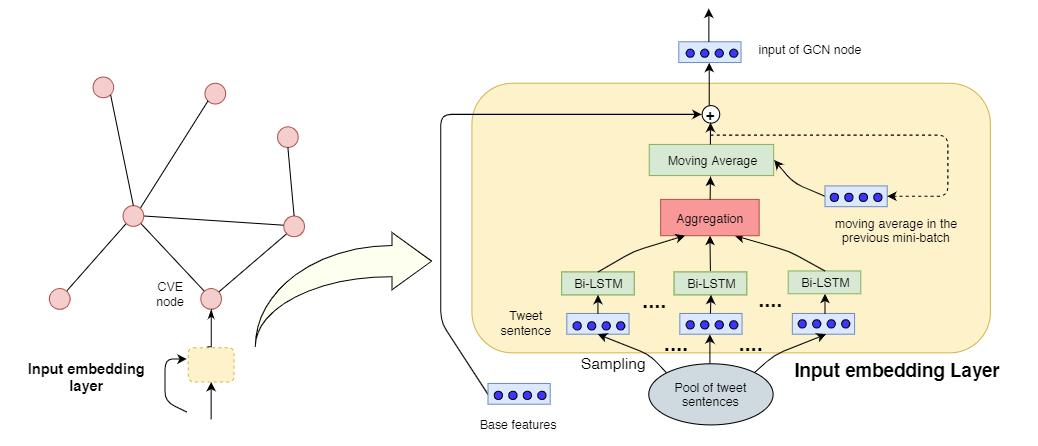
The aim of this work is to use Twitter discussions about vulnerabilities for predicting their severity before the assessments by official agencies. A GCN model is adopted in order to leverage the intrinsic correlations among vulnerabilities for prediction purpose. The graph is constructed in the following way. Each vulnerability is one node. To construct edge among vulnerabilities, tweet-contents related Features (i.e., Bag-of-Words, BoW) are first extracted for each vulnerability. One edge is drawn between two vulnerabilities if the cosine similarity of their BoW features is above a certain threshold. To further capture information contained in tweets, an attention-based input embedding layer is proposed and integrated with one state-of-the-art GCN network. This work could predict the severity of 37.85% volunerabilities at least one week earlier than the official agencies and with a mean absolute error or 1.255.
Attention-based input embedding layer
Overall Architecture